The MaRisk & BAIT published on 16 August 2021 specify the previous regulations and are therefore - with a few exceptions - immediately valid and must be observed. Financial service providers and their (IT) service providers are thus united in an increasingly overarching network of responsibilities. But has this not long been an expression of responsible action? Professional providers who, like afb Application Services AG, see themselves as Business Innovation & Transformation Partners, act as partnership enablers for their customers, are certified and work according to common standards in order to ensure their own compliance as well as that of their customers. This now needs to be reviewed - on both sides - and supplemented if necessary, including with new systems and controls ("SIEM / SOC"). Good for those who now have the right partner at their side ... - an up-to-date overview of the requirements for IT and information security can be found here.
On the occasion of the current publications of the Federal Financial Supervisory Authority on August 16, 2021, financial service providers and service providers such as afb Application Service AG are currently dealing with the implications arising from
- the amendment to the Minimum Requirements for Risk Management (MaRisk) and
- the amendment to the banking supervisory requirements for IT (BAIT)
arise. As in previous years, the regulator's focus remains on IT and information security. As the following (key) requirements are not new, but "only specified", they must be complied with without any further transitional period
- the emergency management requirements described in AT 7.3 of MaRisk,
- the requirements for outsourcing in accordance with AT 9 of MaRisk,
- the requirements resulting from the new chapters added to BAIT with regard to operational information security and, again, IT emergency management.
The "innovations" are also to be implemented with a short deadline of December 31, 2021, with only outsourcing management and risk-bearing capacity extending beyond this date.
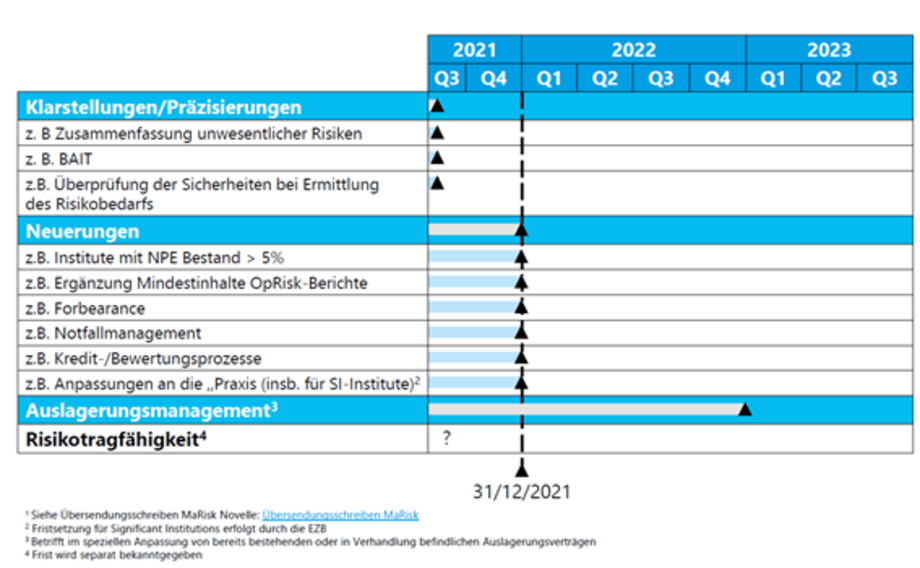
Figure 1: Deadlines from the MaRisk amendment of 16.08.20211, source: zeb
The specifics result from audit practice and the adaptation of European regulations, above all the Guidelines on ICT and security and risk management of the European Banking Authority (EBA), which have been effective since June 30, 2020 and formed an essential basis for the revision of the supervisory requirements for IT in German regulation: they in turn related to the management of risks from information and communication technology (ICT).
This was and is accompanied by special IT-related audits by the German Bundesbank (so-called Section 44 KWG audits) with a focus on "digitalization", e.g. the use of cloud technologies by financial institutions - in addition to traditional special audits on the risk from the use of information technology ("IT risk"). Partly "due to current events", the focus is on the topics of "third-party sourcing" of IT services, increasingly complex IT and cyber security and network security, which must be safeguarded via operational information security - not only in the context of critical infrastructures (KRITIS).
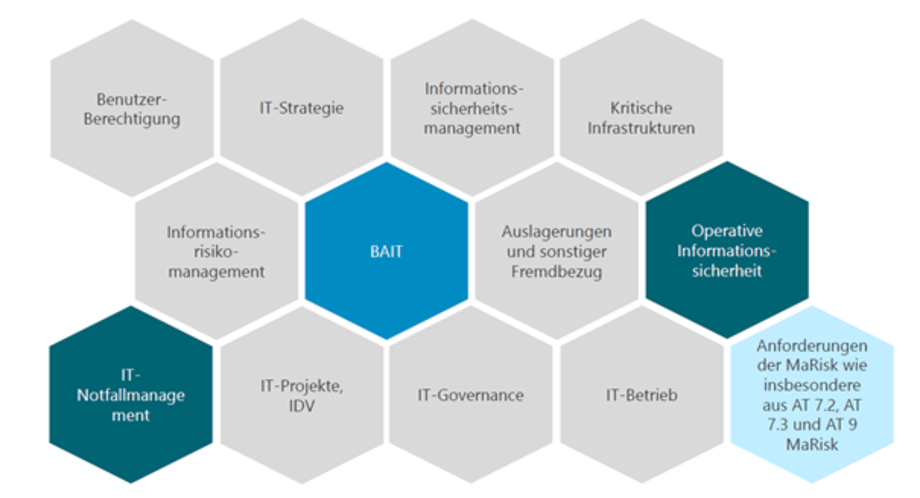
Figure 2: BAIT requirements at a glance, source: Ebner Stolz
According to a current assessment by the auditing firm PwC, the individual subject areas - despite the individuality of each financial services provider - can be roughly clustered as follows into low / medium / high expense categories:
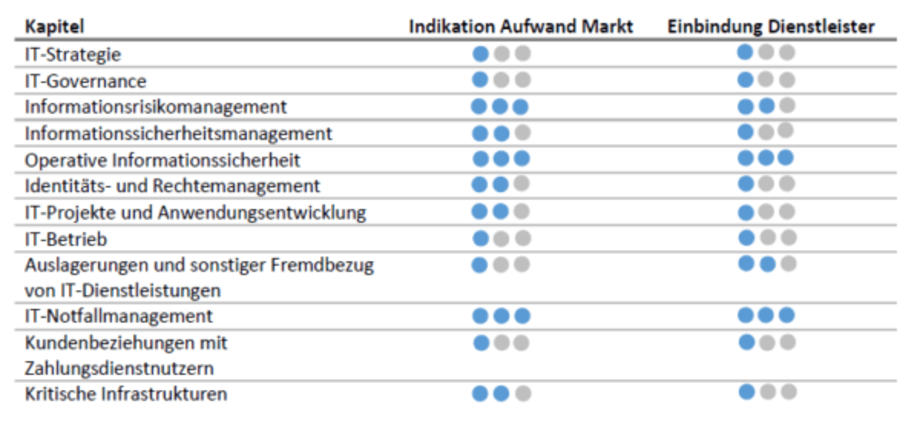
Figure 3: Cost indication for financial service providers and IT providers, source: PwC
It is often not possible without the involvement of the IT service provider - although topics such as IT strategy and IT governance are (or should be) already described, as they are not fundamentally new (see above). For other topics, among others, it is clear that the bulk of the work lies with the financial service provider, as the specifications that need to be observed and implemented by the IT service provider must be specified.
The topics of operational information security and IT emergency management, which - if already contractually regulated in detail and with a large number of measures - at least require an up-to-date review and transfer to a comprehensive business continuity management system, require a full workload on both sides.
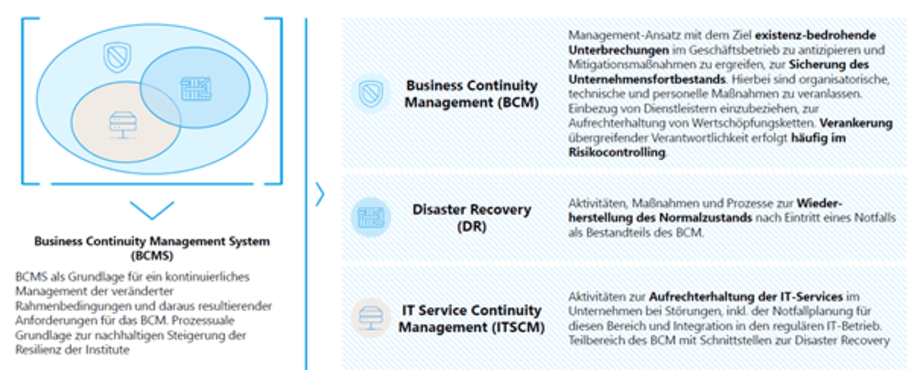
Figure 4: Business Continuity Management System, source: zeb
As part of outsourcing management, IT service providers are faced with audits that reach the scope of a due diligence, in addition to the actual actions to safeguard "IT security" during ongoing operations and emergencies, there is also comprehensive documentation - in line with the principle: "what is not regulated and documented does not exist!"
It is therefore a good thing if the drivers of all measures are not the legislator or the supervisory authority, but rather the inherent self-commitment of the financial service provider to protect its own business model and to protect customer (data) - and in the case of outsourcing, also determine the requirements for an IT service provider. This applies equally to a contracted IT service provider who demonstrates its professionalism by underpinning the responsibility arising from the assumption of services for a financial services provider with the highest standards - in other words: "when it comes to money (and customer data) ..."
Their scope and quality must be based in particular on internal requirements, business activities and the risk situation (see AT 7.2 para. 1 MaRisk). IT systems, the associated IT processes and other components of the information network must ensure the integrity, availability, authenticity and confidentiality of the data (see AT 7.2 para. 2 MaRisk).
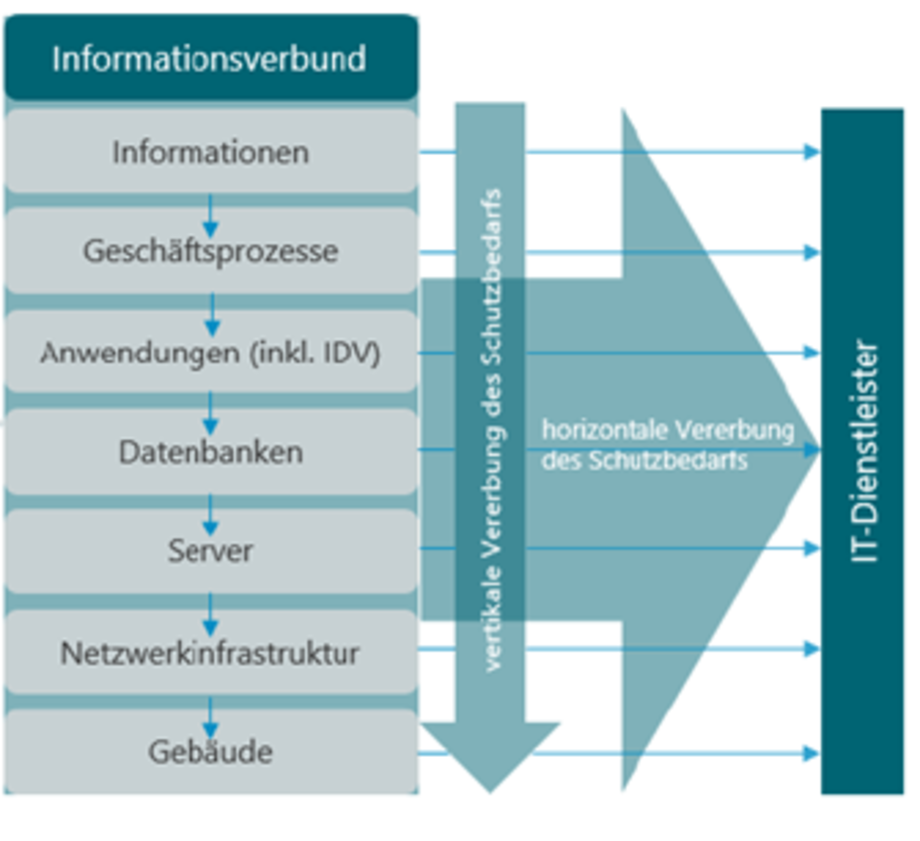
Figure 5: Inclusion of IT service providers in the information network, source: Ebner Stolz
In its actions, the provider is committed to the practices of a "prudent businessman", an enabler acting in partnership with its customer, the financial services provider, is certified (ISO 270XX), works according to fixed process designs (COBIT, ITIL) and uses proven and structuring methods (Scrum) as a basis when further developing its offering.
The orientation towards common standards ensures a structured and proven approach, completeness in terms of conception and implementation as well as actions that are based on best practices.
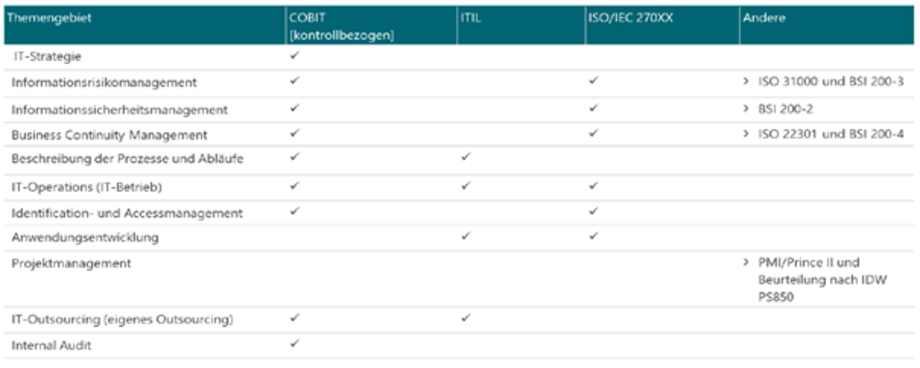
Figure 6: Common standards, source: Ebner Stolz
The IT service provider pays attention to and thus ensures the compliance of its customer, a financial services provider - and thus lays the foundation for many years of successful cooperation. This is why the initial selection decision of a financial service provider is of such fundamental importance for a provider. Only if there is professionalism on both sides can a long-term partnership be formed that - despite the requirement for the financial services provider to always have offers ready that enable a change of service provider - establishes mutual dependencies that cannot be dissolved in the short term.
If the supervisory regulations are understood as the expression of "sensible" and responsible action in terms of business management or security, many things are "actually" taken for granted - for example, a continuous approach based on the PDCA principle:
plan- do- check- act.
In terms of IT security requirements, the following steps, for example, are shared between the financial institution's specialist department (business continuity management) and its own IT or IT service provider (information security management / ISMS):
- a regular analysis of the risk situation that needs to be repeated,
- the resulting analysis of protection requirements,
- the determination of the (target) level of protection with analysis and definition of measures dependent on protection requirements,
- determining the deviations between the actual and target protection levels (gap analysis),
- Risk assessment of the gaps,
- the evaluation and prioritization of measures to reduce / migrate risks or the acceptance of risks (risk management),
- the implementation planning and execution of measures,
- assessing the effectiveness of these measures - and thus re-entering the control loop, if necessary with an adjustment of the target protection level (see above).
In addition to the various vulnerabilities, threats to which companies and therefore also financial service providers are exposed are becoming increasingly important and must be countered by safeguarding cyber security.
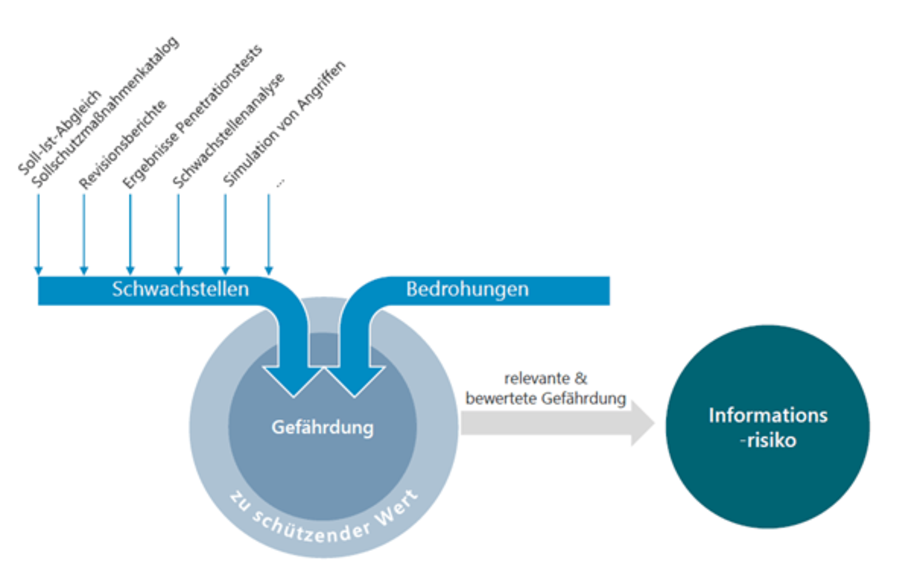
Figure 7: Sources of threats to operational information security, source: Ebner Stolz
NAVAX Software GmbH, which not only creates the software for financial service providers but also operates it, is responsible for the proper configuration of the systems, for example, is responsible for network security and initiates measures resulting from ongoing vulnerability management.
Chapters 4 and 5 of BAIT result in further (new or newly specified) requirements in this regard, in particular
- the implementation of operational measures, e.g. for encryption,
- the regular - mandatory - review of IT systems through vulnerability scans and penetration tests
- ensuring that threats are identified at an early stage (e.g. evaluation of logs and faults) and that a prompt analysis and response is guaranteed,
- the need for guidelines on testing and verification.
The introduction of systems and controls (Security Information and Event Management [SIEM] / Security Operations Center [SOC]) will therefore continue to be a focus in order to meet the objectives of safeguarding IT protection goals and ensuring continuity in the business processes of financial service providers - for companies of all sizes: "Cybercrime knows no principle of proportionality".